CVE-2025-7503
"Shenzhen Liandian Communication Technology LTD OEM IP Camera Telnet Default Credentials Remote Code Execution"
Description
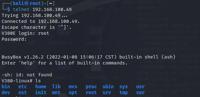
An OEM IP camera manufactured by Shenzhen Liandian Communication Technology LTD exposes a Telnet service (port 23) with undocumented, default credentials. The Telnet service is enabled by default and is not disclosed or configurable via the device’s web interface or user manual. An attacker with network access can authenticate using default credentials and gain root-level shell access to the device. The affected firmware version is AppFHE1_V1.0.6.0 (Kernel: KerFHE1_PTZ_WIFI_V3.1.1, Hardware: HwFHE1_WF6_PTZ_WIFI_20201218). No official fix or firmware update is available, and the vendor could not be contacted. This vulnerability allows for remote code execution and privilege escalation.
INFO
Published Date :
July 11, 2025, 7:15 p.m.
Last Modified :
July 15, 2025, 1:14 p.m.
Remotely Exploit :
Yes !
Source :
1c6b5737-9389-4011-8117-89fa251edfb2
Affected Products
The following products are affected by CVE-2025-7503
vulnerability.
Even if cvefeed.io is aware of the exact versions of the
products
that
are
affected, the information is not represented in the table below.
No affected product recoded yet
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 4.0 | CRITICAL | 1c6b5737-9389-4011-8117-89fa251edfb2 |
Solution
- Disable the Telnet service if possible.
- Restrict network access to the camera's IP address.
- Change default credentials if the interface allows.
Public PoC/Exploit Available at Github
CVE-2025-7503 has a 1 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2025-7503.
| URL | Resource |
|---|---|
| https://github.com/AounShAh/Research-on-v380-cctv-ip-camera |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2025-7503 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2025-7503
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
find Vulnerabilities related to v380 ip camera. Don't Forget to Star this repo
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2025-7503 vulnerability anywhere in the article.

-
Daily CyberSecurity
GPUHammer: First Rowhammer Attack on GDDR6 GPU Memory Induces Bit Flips, Degrades AI Models
For nearly a decade, Rowhammer has haunted DRAM technology, and now it has entered a new field: GPU memory. In a recent security note, NVIDIA confirmed that a proof-of-concept Rowhammer-style attack—d ... Read more
-
Daily CyberSecurity
CVE-2025-7503 (CVSS 10): Hidden Backdoor in Popular IP Camera Grants Hackers Root Access
A critical vulnerability (CVE-2025-7503) has been uncovered in an IP camera manufactured by Shenzhen Liandian Communication Technology LTD. Rated a perfect CVSSv4 score of 10, this flaw gives attacker ... Read more
The following table lists the changes that have been made to the
CVE-2025-7503 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
New CVE Received by 1c6b5737-9389-4011-8117-89fa251edfb2
Jul. 11, 2025
Action Type Old Value New Value Added Description An OEM IP camera manufactured by Shenzhen Liandian Communication Technology LTD exposes a Telnet service (port 23) with undocumented, default credentials. The Telnet service is enabled by default and is not disclosed or configurable via the device’s web interface or user manual. An attacker with network access can authenticate using default credentials and gain root-level shell access to the device. The affected firmware version is AppFHE1_V1.0.6.0 (Kernel: KerFHE1_PTZ_WIFI_V3.1.1, Hardware: HwFHE1_WF6_PTZ_WIFI_20201218). No official fix or firmware update is available, and the vendor could not be contacted. This vulnerability allows for remote code execution and privilege escalation. Added CVSS V4.0 AV:N/AC:L/AT:N/PR:N/UI:N/VC:H/VI:H/VA:H/SC:H/SI:H/SA:H/E:X/CR:X/IR:X/AR:X/MAV:X/MAC:X/MAT:X/MPR:X/MUI:X/MVC:X/MVI:X/MVA:X/MSC:X/MSI:X/MSA:X/S:X/AU:X/R:X/V:X/RE:X/U:Red Added CWE CWE-798 Added Reference https://github.com/AounShAh/Research-on-v380-cctv-ip-camera


